cryptovision CAmelot
With CAmelot, you can build a public key infrastructure (PKI) that exactly fits your requirements. Existing CAmelot PKIs can be easily modified and extended. As one of the most flexible PKI solutions worldwide, CAmelot supports both corporate and government PKIs.
If spies and hackers threaten your IT systems, you should react – before it is too late. Above all, authentication, digital signature and encryption are effective antidotes. For these security measures to work, you need private keys and digital certificates. The management of digital certificates is an important task. The components required for this are known as public key infrastructure (PKI).
A PKI is always a very individual infrastructure. The exact implementation always depends on the IT environment, security requirements, the desired applications and many other factors. Often an existing PKI has to be changed afterwards. CAmelot, a product of cryptovision, is a highly flexible solution for the operation of a PKI that takes these requirements into account.
With CAmelot you can build a PKI that is tailor-made for your individual needs. Existing CAmelot PKIs are easy to change and extend. One of the reasons CAmelot is so flexible is that it is based on a completely modular architecture. In addition to the standard modules, further modules can be developed according to your requirements.
As one of the most flexible PKI solutions worldwide, CAmelot supports both enterprise PKIs (X.509 certificates) and authority PKIs (CV certificates). In addition, CAmelot’s modular architecture enables different security levels. High security architectures can thus be realized as well as cost-effective infrastructures for pragmatic security requirements. Unneeded modules are omitted, which also significantly simplifies administration.
FAQ
Why do I need a PKI?
Private and public keys play a major role for authentication, encryption, and digital signature. However, a private/public key pair is only of use if it is bound to a digital identity (this can be a person or a device). This binding is achieved with a digital certificate. A Public Key Infrastructure (PKI) is the combination of components and processes necessary for managing digital certificates. Typical parts of a PKI include a certification authority, a certificate repository, and PKI applications.
What is a PKI workflow?
A PKI workflow is defined by the sequence of persons and components that are involved in a PKI process – especially certificate enrollment and renewal – and by the data that is processed. Workflow design plays a crucial role in a PKI. In order to make a PKI process effective, secure, and compliant to certain rules, it is necessary to specify exactly, which party processes which data in which order.
What is a PKI client?
A PKI client is a component that is installed on the user platform. It is responsible for client-side communication with other PKI components. It supports the user in using and administering his private keys and certificates. For instance, a PKI client can automatically renew a digital certificate when it expires.
Who uses CAmelot?
CAmelot is used (among others) by the following customers:
- Identity authorities of emerging nations: Citizens of several emerging nations receive eID cards with private keys and certificates.
- German defense supplier: Uses CAmelot for authentication.
- Car manufacturer: A Japanese car manufacturer uses CAmelot for protecting the internal IT infrastructure.
The Technical Part
Supported systems
- Windows Server 2008/2012 R2
- Redhat 6/7 64bit
- CentOS 6/7 64bit
- Any LDAP server which supports the entryDN attribute (RFC 5020)
- HSMs from Utimaco, Thales (nCipher), Bull, Gemalto (SafeNet)
MODULES, BASICS, KEY FEATURES, COMPARISONS
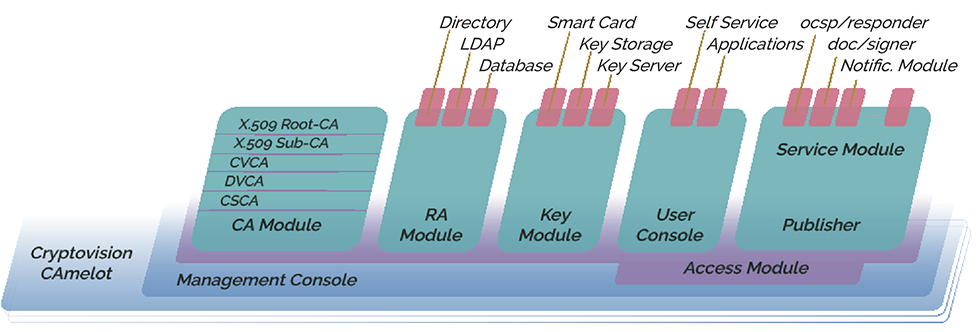
CAmelot contains the following modules
-
- Protocol Handler Modules: This Module type communicates with control units, especially with a management console.
- Key Manager Modules: Key manager Modules communicate with the key stores usedby CAmelot, typically smart cards, HardwareSecurity Modules (HSMs) or key files.
- Publisher Modules: Modules of this type are responsible for publishing digital certificates generated by CAmelot. Especially, Modules for LDAP servers, databases, and files can be used.
- Certifier Modules: Modules of this type assemble the content of digital certificates and prepare them for signing. There are Modules for X.509 certificates and card verifiable (CV) certificates.
- CA Modules: This is the core component, responsible for generating and signing digital certificates.
- Certificate Template Modules: A Certificate Template Module provides one or more specific certificate extensions which are encoded in a certificate.
- Access Module: The Access Module (there is only one of its kind) is responsible for access control within the CAmelot architecture. It verifies the access conditions from external systems and also for the internal connections between the Modules.
CAmelot is a Certification Authority (CA) software. The CA is the core component of a Public Key Infrastructure (PKI).
For Individual PKIs
With CAmelot you can easily configure your own individual PKI architecture. CAmelot supports all scenarios from simple PKIs with one CA to complex certification hierarchies. Changes in the PKI setting are easily possible.
For Extensible PKIs
With CAmelot you can change or extend your PKI without touching the system core. You can choose from many existing modules. Additional modules can be developed, existing ones can be customized.
Certificates for eIDs
CAmelot is an ideal solution for electronic identity documents (eIDs). It supports both X.509 and card verifiable (CV) digital certificates. It can also be operated as an ICAO Document Signer. Due to its modularity it easily scales to hundreds of millions of users.
Certificates for Enterprises
CAmelot is ideally suitable for enterprise certificate lifecycle management. Due to its modular architecture it can be easily integrated into existing IT environments and provisioning processes. Instead of introducing a new infrastructure CAmelot is designed according to the philosophy that existing infrastructure should be used and that different components with similar tasks should be avoided.
Platform-independent
CAmelot is completely realized in JAVA. Therefore, it can be operated on many different platforms.
High Security
Based on the modular architecture CAmelot supports PKIs on different security levels. From a high security PKI (e.g. for corporate infrastructures) to a cost-effective PKI with medium security requirements all scenarios are possible. CAmelot supports HSMs, flexible roles, strong admin authentication and more.
Advanced Features
CAmelot supports a sophisticated logging function, several kinds of auto-enrolment and many other advanced features.
General
- Hierarchies, SubCA, Meta-PKI
- Multi-tenancy
- Logging, monitoring, scaling
- Smart card support
Algorithms and standards
- X.509 and CV
- CMC
- EACv2 / TR3129
- OCSP
- ECC and RSA
Security
- HSM, dual security
- Certificate based login
- Workflow, signed approval
Convenience
- Auto-Enrolment
- Maximum certificate profile flexibility
- Card protection with fingerprint
- Easy regionalization

Pendragon
Pendragon is a PKI client from cryptovision. Pendragon offers the maximum usability possible within a PKI. Pendragon perfectly complements a PKI whose certificates are created by CAmelot, but can also be used with any other PKI.
Pendragon allows the user to handle different keys and certificates via the same user interface, even if they are stored in different memories (Smartcard, Windows Keystore, Java Key Store).
The functionality of Pendragon is based on the life cycle of a digital certificate. The first certificate uses Pendragon as a security anchor to generate further certificates (e.g. for encryption or identity verification on the Internet), whereby no user interaction other than confirmation is required. The replacement of a certificate shortly before the expiry date is similarly user-friendly – the user does not notice anything other than a confirmation by mouse click.
The advantages of Pendragon result from the interaction with CAmelot and the workflow engine Shalott. With the help of these solutions, an almost arbitrary process for the generation of certificates can be defined which, in addition to the user-friendly application for a certificate, provides for the confirmation of a certificate generation by an administrator, for example.
Key Features
- User-friendly certificate generation
- User-friendly certificate renewal
- Holistic handling of all keys on one PC, even when different key stores are used
PKI Management System
The PKI Management System is the central point for the administration of certificates and private keys, as well as for the management of various connected certification authorities.
The PKI Management System consists of a workflow system with web interfaces for end users, PKI operators including workflow designer and a management console for the PKI administrator as a system of information and tasks. This central component is used to design and implement all relevant workflows within a PKI. The integration of any data sources (e.g. identity management system) is just as possible as a dual control principle and incompatibility regulations.
Key Features
- Management of keys, certificates and certification authorities via a clearly arranged interface
- Arbitrary workflows for PKI processes can be easily implemented
- Implementation of security policies configurable